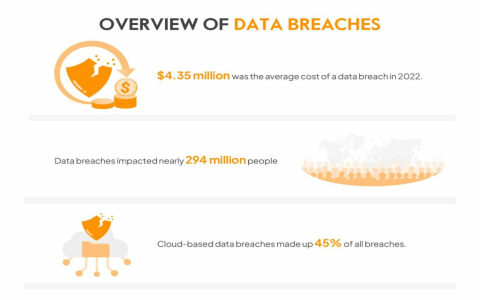
In 2025, a data breach triggers immediate financial penalties, reputational harm, and regulatory scrutiny, exacerbated by advanced threats like AI-powered attacks and quantum risks. Swift, structured response is critical to mitigate impact.
Step 1: Contain the Breach
Isolate affected systems instantly to halt unauthorized access. Disable compromised networks, servers, or applications, and deploy automated tools for real-time threat detection.
Step 2: Notify Stakeholders
Comply with global regulations by informing regulators within 72 hours, and communicate transparently with affected customers to maintain trust. Tailor messages based on 2025 privacy laws evolution.
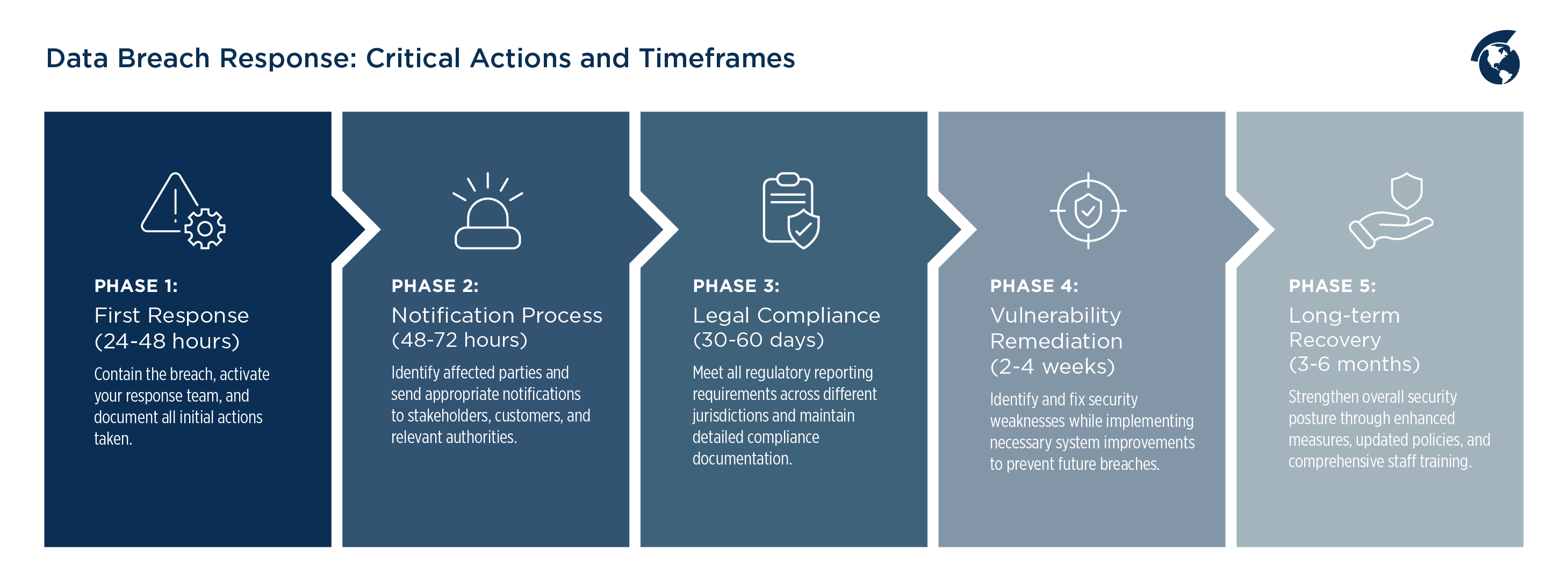
Step 3: Initiate Forensics Investigation
Engage third-party experts to analyze breach scope, origin, and impact using AI-driven tools. Document findings meticulously for legal compliance and root-cause identification.
Step 4: Remediate Vulnerabilities
Patch exploited weaknesses and restore systems from secure backups. Incorporate zero-trust architecture and quantum-resistant encryption to fortify defenses against emerging 2025 threats.
Step 5: Enhance Resilience
Update incident response plans and integrate continuous monitoring. Conduct regular employee training and simulate breaches to future-proof security posture in an evolving landscape.